Securing MDM-managed devices with the gateway
If you are using a Mobile Device Management (MDM) solution with the Blue Cedar Connect Gateway to manage your mobile devices, the gateway provides an optional security feature called external validation that ensures only MDM-managed devices are allowed to certificate enroll and connect to the gateway.
About Blue Cedar external validation of MDM-managed devices
The process of external validation requires a validation key (often the media access control address/“MAC address") for the managed device, so that the MDM server can confirm if the device is registered with the MDM service and if the device is compliant with the MDM policies. The Blue Cedar-secured app submits a request containing its user credentials to the gateway for authentication. The gateway then checks the user credentials against the authentication provider for that user. At the same time (if configured), the gateway performs a query to validate externally whether the mobile device is MDM-managed and compliant. You must configure the gateway to communicate with the appropriate MDM server using an MDM RESTful API before the gateway can validate a device.
For iOS devices, the MDM server pushes the secured app and device-related info (called the “MDM managed app configuration payload”, which includes the MAC address) to the managed device. The gateway can identify Android MAC addresses without the MDM server.
This figure summarizes the external validation process that involves the MDM provider, the mobile device user, and the gateway.
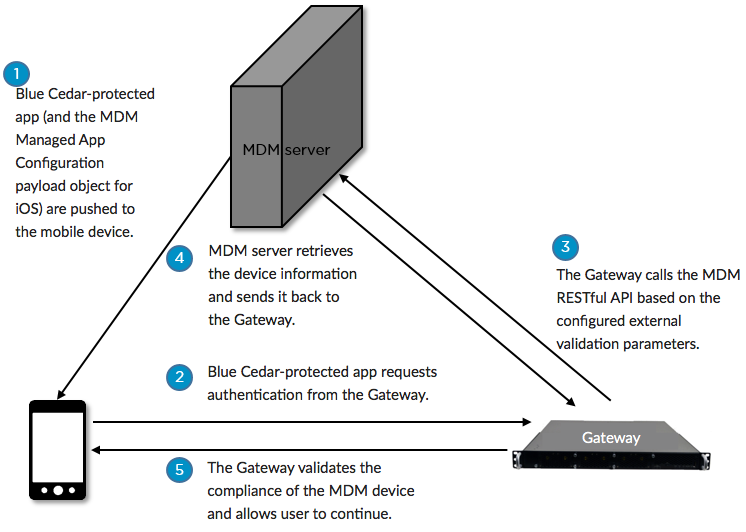
Blue Cedar Connect Gateway External Validation Process
The gateway supports the external validation RESTful API implemented by the following MDM vendors:
- AirWatch
- Citrix
- Fiberlink MaaS360
- Good Technology
- MobileIron
- SAP Afaria
Please consult each vendor’s MDM documentation for the required configuration information for implementing that MDM RESTful API.
Note: The REST API query must return both registration status and compliance status. Devices found to be both registered and compliant are allowed to continue. The gateway denies access for non-compliant and non-registered devices according to the configuration settings. This figure shows the step where non-compliance is evaluated.
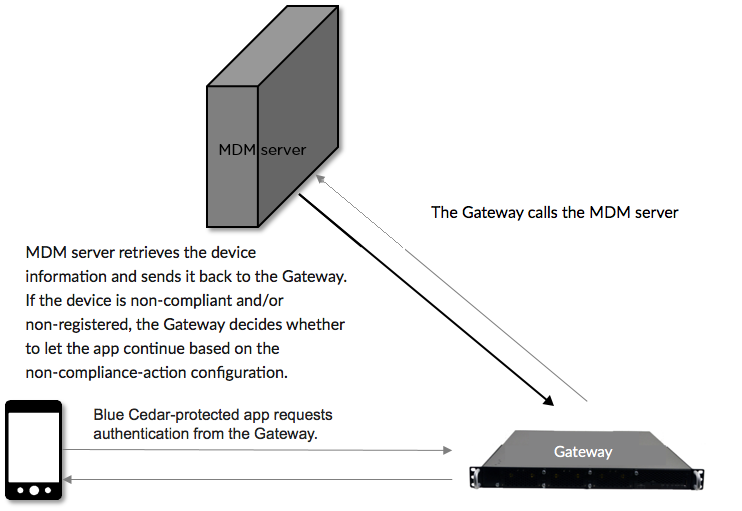
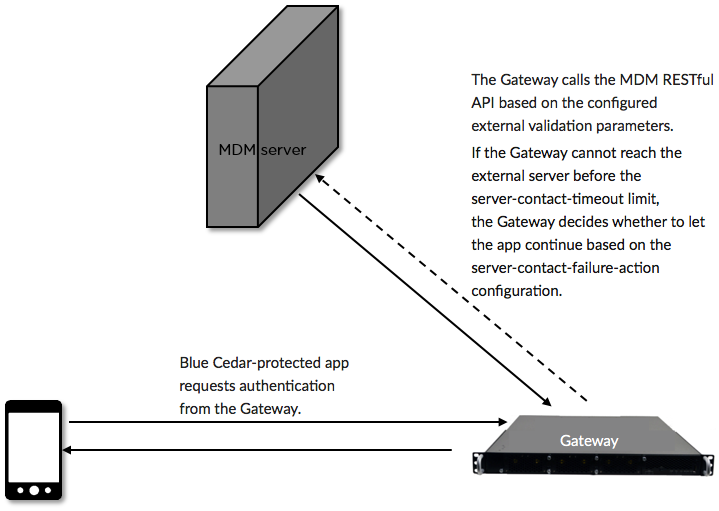
If the MDM server is unreachable, the attempt to connect times out and the gateway decides whether to let the app continue based on configuration settings:
Prerequisites to performing external validation
There are two prerequisites for performing external validation of MDM-managed devices:
- (Android and iOS devices) To enroll an MDM-managed device with the gateway, the verification key (MAC address) of the device that is connecting to the gateway must be the same verification key of the device that is registered with the MDM server. Devices must be registered with the MDM server and be compliant with any MDM-enforced policies in order for the gateway to permit them to perform easy certificate enrollment.
- (iOS devices only) You must configure the MDM server with the verification key (MAC address) of the device before the gateway can perform external validation of the MDM-managed device. The external validation feature will not work unless the required configuration payload is pushed down from the MDM server to the device. On the MDM server, you should configure the Managed App Configuration section to include the macAddress key/value at the top level of the configuration payload object.
Configuring the gateway for MDM external validation
Configure external validation within the scope of a particular authentication group (auth-group). The gateway applies the external validation to any authentication attempts made by the user to authenticate against that auth-group.
Note: Make sure you are configuring for the correct authentication group or else external validation does not work.
This is the template for the CLI command:
% set aaa auth-group groupname external-validation mobile-device-management enable true
url MDMservice_URL username user password string enrollment-only boolean identity-cert-name certname
non-compliance-action action server-contact-failure-action action server-contact-timeout value| Option | Description |
|---|---|
| auth-group groupname | Required. Specify the authentication group for the gateway to apply external validation against. |
| default-failure-reason string | Default failure reason sent to the client upon authentication failure if none was sent by the MDM server. |
| default-remediation string | Default failure remediation sent to the client upon authentication failure if none was sent by the MDM server. |
| enable boolean | Required.
|
| enrollment-only boolean | Optional. This option restricts external validation to perform at enrollment only. When set to true, you must also enable easy certificate enrollment. For details about enabling this feature, see Setting up certificate enrollment with the gateway. The external validation is only performed when a secured app goes through easy certificate enrollment. To perform external validation at all authentication steps (at enrollment and after), you do not need to enable easy certificate enrollment—just set enrollment-only to false.
|
| external-validation mobile-device-management | Required. Specify MDM external validation. |
| identity-cert-name certname | Name of identity-certificate to use for mutual SSL authentication with the ISE compliant MDM server. |
| non-compliance-action action | Optional. Whether to allow the admin to let users complete authentication if the user's device is non-compliant. Possible values:
|
| server-contact-failure-action action | Optional. Whether to allow the admin to let users complete authentication if the external validation server is not reachable. Possible values:
|
| server-contact-timeout value | Optional. Upper limit on the time (in seconds) the gateway should wait for the external validation server to respond. Default: 20 Range: 5–120 seconds |
| url MDMservice_URL | Required. Specify the link for the MDM service. Note: Most MDM services run the RESTful API call on a standard port. However, other MDM providers may run this particular function on a non-standard port. Blue Cedar recommends that you read your MDM server’s documentation to determine if a port change is necessary. If it is necessary, then include the port in the URL value, as in https://mdmserver.company.com:1234. |
| username user | HTTP Basic Authentication username. (Optional.) |
| password string | HTTP Basic Authentication password. (Required if username is supplied.) Note: The MDM REST API specification only allows Basic authentication or no authentication. If the username and password fields are empty, the gateway uses no authentication. |
Example
% set aaa auth-group groupname external-validation mobile-device-management enable true
url http://mdm.acme.com username jbrown password string enrollment-only false non-compliance-action deny
server-contact-failure-action allow-now server-contact-timeout 5You can confirm the configuration by entering this CLI command in configuration mode:
% show aaa auth-group defaultThis is the expected output:
auth-group default {
external-validation {
mobile-device-management {
enable true;
enrollment-only false;
password TU9DREFSAAJWEUcdZlrftDRjpS0uFEsX1wAAAAAAAAAdHvtVTK/Fsqv+l0Mc/pMmMn3mtQcUsJL7JJrE4wjBHKHGivKzaKT+f+H+E5FXLI/NT0wNoNAKHRWFxp0vVaExl0xhkjTo9N3DhPxzS5bCje0AiE6UBOP02O3W2SzoVcrk2X+vJ2nCnLyiOAws6eY5q0JlaYKgVpEpQm/Ope39ldjxztfN5EY1YFmeyLXnnLz5WDdMCqyO6qSJWSMASLe7lp6YYEldOYQuOprORTK3mjbXhFDyEsn4wYBh5C2XhmOYU4etxaLN1jPBvSxdpylfGcNKgCzpX6AcPME4f0npdV8TGa8Ix7HDQQBGZIO92JnUHIo550KTkD+ASjrT21gqHge2/xkX+TKz8zm1YHY9UMeMgqZo2556dJvHDggPRAs=;
username jbrown;
url http://cisco.acme.com;
server-contact-timeout 5;
non-compliance-action deny;
server-contact-failure-action allow-now;
}
}