Understanding certificates used by Blue Cedar products
Overview of certificates
Server certificates (SSL identity certificates) are used to identify a server. HTTPS web sites (vs non-SSL HTTP web sites) require the server to have a valid and trusted server certificate. This certificate helps establish a trust between the server and endpoint and allows the endpoint to validate that the server is valid. Apart from authentication, SSL certificates are also used for encrypting data in transit between the server and user.
The Blue Cedar gateway appliance 3.x used IKE identity certificates, but the Blue Cedar Connect Gateway 4.x uses HTTPS / SSL certificates.
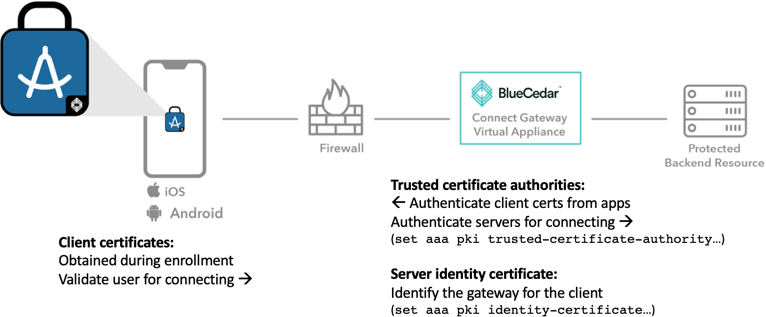
Client certificates (SSL identity certificates) are used to identify a client (user), that is, the mobile app user. The Blue Cedar mobile client obtains a client certificate as part of the enrollment process. This client certificate can be presented to web servers and used to skip login prompts from web servers, resulting in a smoother mobile experience. Client certificates are not used for encryption, just for validation.
- Certificate enrollment: The Blue Cedar Connect Gateway provides certificate enrollment for the user to enroll client certificates from Blue Cedar-protected apps to the gateway. See Setting up certificate enrollment with the gateway. The gateway supports both SCEP and EST certificate enrollment protocols. See SCEP vs EST to compare the protocols. See Configuring certificate enrollment for the gateway to choose one.
Blue Cedar Enforce policies that manage certificates include:
- Secure Microtunnel policy: Platform admin provides a trusted certificate so the app can validate the identity of the Gateway itself.
The Blue Cedar Accelerator for Microsoft also includes the Secure Microtunnel policy. - Trusted Server Certificates policy:
- On the Blue Cedar Platform: Platform admin configures trusted server certificates per app.
- On the Blue Cedar Connect Gateway: Platform admin configures a list of certificate authorities trusted by the gateway. These CAs can authenticate client certificates presented by integrated apps and servers that the gateway is securely connecting to.
- Client Certificates: (Optional) Platform admin defines which sites are presented with client certificates and which sites are not. (Client certificates are obtained during user enrollment; this policy does not manage the certificates themselves.)
The gateway always uses the client certificate to identify the client.
Configuring certificates on the Blue Cedar Connect Gateway:
See this page for details about configuring certificates and certificate authorities for your public key infrastructure on the gateway.
Troubleshooting certificate issues
Server certificate for the Blue Cedar Connect Gateway is not trusted
Issue:
An app (integrated with the Blue Cedar Cloud Platform) exits at launch with the error "The server certificate for the Blue Cedar Connect Gateway is not trusted. Please contact your administrator."
Solution:
The policies that are integrated with the app do not have the correct trusted server certificate.
To fix this issue, you need the Issuer certificate (CA certificate) of the server's identity certificate. (This CA certificate is part of your PKI infrastructure.)
- On the Blue Cedar Cloud Platform, edit the Secure Microtunnel policy.
- Upload the CA certificate to the Gateway Certificate field.
- Re-integrate the app with the updated policy.
Note: The Trusted Server Certificates list in the Secure Microtunnel policy applies to CA certificates used to validate URLs requested by the app, not to the gateway cerftificate.
Client certificate verification failed
Issue:
An app (integrated with the Blue Cedar Cloud Platform) exits at launch with the error "Client certificate verification failed. Please contact your administrator."
Solution:
The gateway cannot verify the client certificate. To fix this issue, check the logs. This issue usually means the CA certificate that issued the client certificate is not configured in the gateway's trusted certificates. See https://apollo.bluecedar.com/connect-gateway-doc/managing-authentication/configuring-aaa/configuring-aaa-public-key-infrastructure for details.
