Policy Console IT Administrator Guide
Injecting mobile app security with Blue Cedar Enterprise
The Blue Cedar Policy Console allows you to inject app security policies into iOS and Android apps. App security policies are business logic rules that you use to protect apps before the secured apps are deployed to end users. Blue Cedar secures the apps post development, so you don’t need to access the original source code or to install a separate client on your users’ devices. This process protects mobile apps with fine-grained security and usage policies, giving you self-defending apps that protect corporate data, limit usage, and control access without modifying user experience.
The console is integrated with the Blue Cedar Gateway; together they provide a complete solution for injecting security to protect the enterprise data—from the app on a mobile device to the backend systems behind your corporate firewall.
While the injectable security protects an app and its data on a mobile device, the Blue Cedar Gateway provides end-to-end secure microtunnels to and from your Blue Cedar-protected mobile apps to the enterprise backend on a massive scale. The gateway is a network appliance that securely authenticates the connectivity of mobile apps to sensitive internal enterprise resources through its secure microtunnels. Together the policy console and the gateway enable very high density end-to-end security for enterprise apps with high availability and redundancy.
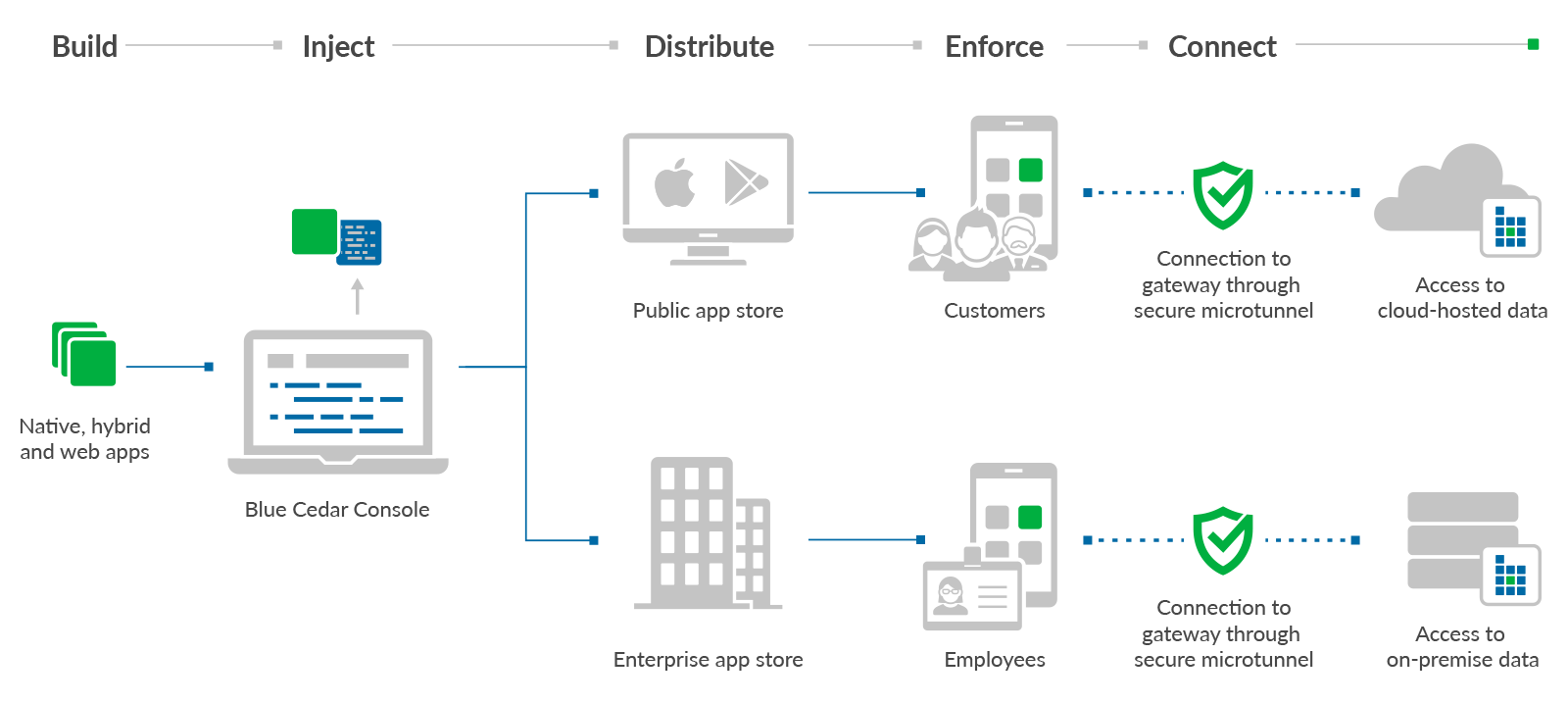
The heart of Blue Cedar Enterprise is the Blue Cedar Gateway. The gateway enables unique authentication, identity, and trust relationships with any Blue Cedar-protected app. Combined with its location in an enterprise’s network, the gateway can extend that relationship to any backend service, making Blue Cedar Enterprise a platform for all app transaction assurance, such as app performance monitoring and security event analysis for your business. The gateway also lets you dynamically configure and apply policies without having to re-secure the app.
To use the policy console, follow an automated process:
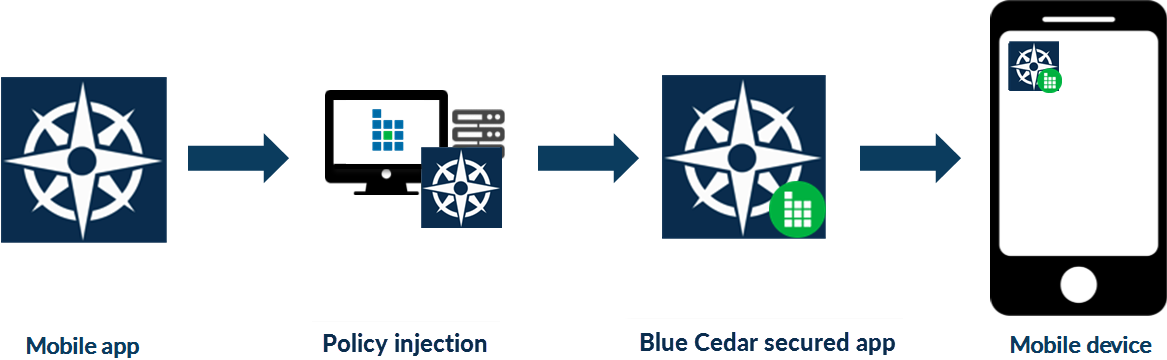
The IT administrator loads a finished enterprise app into the policy console and sets app security and usage policies.
The policy console generates a new variation of the enterprise app with the configurable policies injected into the app itself. This process does not require SDK integration or access to source code.
The administrator adds the newly secured app to an app store for distribution to end users’ mobile devices. The app store can be public (Apple App Store or Google Play) or private (in-house or MDM-supported).
End users interact with their enterprise apps as before, except now with security policies in effect.
If you have set up a Blue Cedar gateway to handle the secure microtunnels, then you can take full advantage of the power of Blue Cedar Enterprise.