Configuring OAuth authorization of gateway users
The Blue Cedar Connect Gateway allows you to use an OAuth server as an authentication provider for authenticating users. The gateway can authenticate against any server that can perform validation of an OAuth token. To enable this feature, configure an OAuth authentication provider with the server’s URL.
To use the OAuth authentication feature on the gateway if the URL is HTTPS, complete these two steps before you configure the gateway:
- Make sure the remote server has installed a certificate that is trusted by the gateway. The certificate for the remote server is issued by a trusted certificate authority (CA).
- Configure the gateway for the trusted-certificate-authority that issued the certificate for the remote server. This configuration step registers the CA as trusted by the gateway. For details, see “Configuring Trusted Certificates” in Configuring AAA Public Key Infrastructure.
For a full description of available configuration attributes, see your OAuth documentation.
To verify an OAuth token for the gateway to authenticate its users:
- Set the auth-provider type as oauth.
- Set the name of the OAuth server.
- Set the URL of the OAuth server.
% set aaa auth-provider oauth provider-id auth-url url| Element | Value |
|---|---|
| oauth provider-id | Required. Descriptive name for the OAuth server |
| auth-url url | Required. URL for the OAuth server. |
If the URL for the OAuth server uses HTTPS, you must provide the CA certificates that signed the URL's server certificate. This is necessary for HTTPS validation.
- Visit the auth-url in a web browser. For example, https://graph.microsoft.com/v1.0/me.
- Download the certificate from the browser. In this example, you need both the Baltimore CyberTrust Root CA and the Microsoft IT TLS CA 2 certificates.
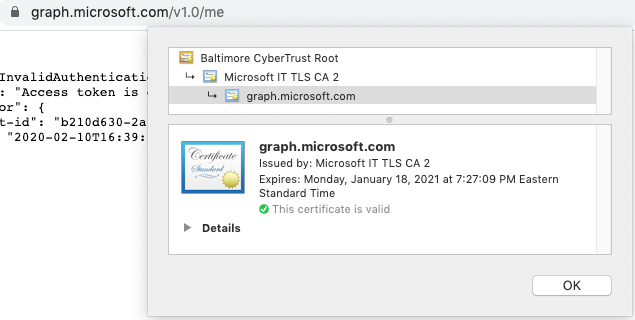
- Enter each certificate in the gateway's trusted certificate list:
% set aaa pki trusted-certificate-authority cert-name certificate-pem-data
Enter/paste Base64 PEM data. Enter Ctl-D to complete.
----BEGIN CERTIFICATE---
MIIDUzCCAjugAwIBAgIIDz3ujuueapEwDQYJKoZIhvcNAQEFBTEwNzEPMA0GA1UEAwwGQm9sdENBMRMwEQYDVQQLDApDZWRhciBIaWxsMQ8wDQYDVZZKDAZNb2NhbmEwHhcNMTMwNDIzMTUxNTE4WhcNMjMwNDIxMTUxNTE4WjA3MQ8wDQYDVQQDDAZCb2x0Q0ExEzARBgNVBAsMCkNlZGFyIEhpbGwxDzANBgNVBAoMBk1vY2FuYTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKiYrcp0i0zf5bUDfn4DGzLZNGCew0Pm94pX+QsqRdQgoNl/YddqWB2gygGhUMS67GFs+WZ0I3d8exaupFVtWJ3lU/jI3jk7lqE4g/+EgShR82D9d08nx2glqq6v46/pLcyVmRwZ4gpt7X+741/S6VSF4ldROnNIGwzkZUHDDKRKYyXjS4IFA7bDvxc9qK9yYCg0l6deUw+DA/jIHEBRq3kz0AGFs1ObK/RyfoIvIwTZp9/OZNl1E4gDR692ebUGG7VX1vke1T79ThjF2W8vjVc0tZITXrCyd3B1MMpsjVTfsaTm9wu6Q9O+oaq9X7ibqdpRzBxGfAE9ezp77UjfUFcCAwEAAaNjMGEwHQYDVR0OBBYEFOH5TcESHbGZCjDHXwpB7NhJjaGTMA8GA1UdEwEB/wQFMAMBAf8wHwYDVR0jBBgwFoAU4flNwRIdsZkKMMdfCkHs2EmNoZMwDgYDVR0PAQH/BAQDAgGGMA0GCSqGSIb3DQEBBQUAA4IBAQB5kJ/CML39GU+IJnDm1T+bYcZCLStxf/grmQZF7r+31V2/kPb+IoxvmnJ0WjF+2G9q72RSFB91d8ZJsLq02RxfUxbtRyGVsGID/NZusPN/PcUbmHUPzvbGfhdpbY7yvpu+L4g9pyHKzt00zIvXIHyXSz5XjHzVjP5yAyvN/4JvfV44OcakqttKMb06WJP5B8u7d+Hf9H1xzVu9BiTxOxxiiqeI3R9dFJxzRYc/fO8njwtOHe4bCsr9gzwxG0yESWQnTTkP5xYZhTpNCLM9Rpibv7cQUrh0qxgaXKvnRjH7z6u9V3VrkMxD3kaCuhRcSV/S2SLGg0JB5nmYhR1Lu8bu
---END CERTIFICATE----| Element | Value |
|---|---|
| cert-name | Required. Descriptive name for the trusted cert. |
Using OAuth tokens for apps integrated with Intune
If you are using the Connect Gateway with apps integrated with the Blue Cedar Accelerator for Microsoft, you must use a custom authentication policy to use the Intune login (OAuth token) on the device to also authenticate with the Connect Gateway. Configure custom authentication policies on the Blue Cedar Platform. See Using the Blue Cedar Accelerator for Microsoft for details.
