Configuring Active Directory to authenticate gateway users
You can configure Active Directory user authentication for the Blue Cedar Connect Gateway by restricting username formats and configuring the AD domains. After configuring the domains (described on this page), finish configuring the connections between the Gateway and Active Directory (see Next steps).
Note: The gateway supports AD running on Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012 R2.
Restricting AD username formats
You can restrict the format of usernames that are valid for Active Directory at authentication. By default, the gateway does not restrict username format, and allows any of the standard formats described below.
Use the restrict-username-format option to force usernames to confirm of one of these schemes. This restriction also affects what ends up in the common name of the certificate with standard authentication. If a username does not conform, the gateway denies it, and a debug-level log records the reason.
% set aaa auth-provider active-directory-server name_of_server
restrict-username-format username_option| Username option | Description |
|---|---|
| downlevel-only | Username formatted as DOMAIN\username, for example, qwe.com\jdoe |
| unrestricted | No restrictions—all username formats are accepted. |
| upn-only | User principal name format, for example, jdoe@qwe.com. |
| username-only | Username without domain, for example, jdoe. |
Configuring the gateway for a single AD domain
Use this template to configure a single Active Directory domain for the gateway to authenticate its users:
% set aaa auth-provider active-directory-server name_of_server domain-name domain_nameAll users, groups, and group privileges are defined on the Active Directory server. See the Active Directory documentation for the procedures in configuring users, groups, and privileges.
You can have up to 20 Active Directory servers configured for the gateway at any time. If you try to configure more than 20 AD servers, the CLI throws an error.
Example
The following example sets an AD authentication provider name ADServ03R2 to domain name example.com.
% set aaa auth-provider active-directory-server ADServ03R2 domain-name example.com
% commit
Commit succeeded.
% show aaa auth-provider active-directory-server
active-directory-server ADServ03R2 {
domain-name example.com;
restrict-username-format unrestricted;
}Configuring the gateway for multiple AD domains
When a user authenticates to an Active Directory with multiple domains, they typically must prepend their username with the name of the domain that they belong to (such as sales\janesmith or finance\stevebrown). However, users frequently forget their domain name and thus block themselves when logging in to authenticate themselves.
To solve this problem, the gateway supports the ability of its users to authenticate to an AD domain without having to prepend their username with the name of the domain that they belong to. In other words, the users only have to enter their unique usernames (for example, janesmith or stevebrown) along with their password to authenticate themselves against an AD infrastructure that has multiple domains.
To enable this functionality, use one of these options:
For the AD domain that the gateway is connected to (and the domain is not a root domain), use this template:
BASH% set aaa auth-provider active-directory-server name_of_AD_server domain-name IP_address_or_server_name
For all other AD domains that belong to the same AD forest and none of the domains is not a root domain, use this template:
BASH% set aaa auth-provider active-directory-server name_of_AD_server domain-name IP_address_or_server_name_of_the_domain authentication-prefix name_of_prefix
The following example shows how to use both of these CLI commands to configure the gateway for multiple AD domains.
The ability of users to authenticate to an AD domain without having to prepend their username (with the name of the domain that they belong to) works when you have unique usernames across domains. However, if you have conflicting usernames, users must log in with a long-form username (such as 'DOMAIN\username').
Example
The diagram below shows an Active Directory deployment that features five domains within the win.company.com domain. The gateway is joined to the servers.win.company.com domain, but users are also present in the region.win.company.com domain and other child domains. All domains are associated into an AD forest with two-way transitive trusts established between each domain. The administrator would like users located in region, subregion1, and subregion2 to be able to authenticate using their unique usernames. The following figure describes these domain relationships in an AD forest of domains.
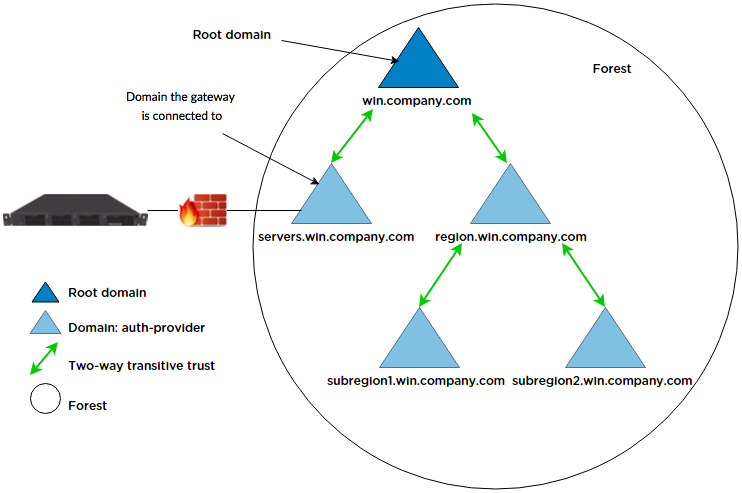
Active Directory forest and its domains
Based on this figure, the following sample CLI commands illustrate how to configure the gateway for multiple AD domains:
AD domain that is connect to the gateway
% set aaa auth-provider active-directory-server servers
domain-name servers.win.company.com| Element | Description |
|---|---|
| servers | The name of the Active Directory service |
| servers.win.company.com | The domain name of the AD domain that the gateway is joined to. |
REGION domain
% set aaa auth-provider active-directory-server region
domain-name region.win.company.com authentication-prefix REGION| Element | Description |
|---|---|
| region | Name of the Active Directory service |
| region.win.company.com | Domain name for the AD domain |
| REGION | Authentication prefix that identifies the AD domain. NOTE: Every AD domain has a short name (such as "REGION\jsmith") |
SUBREGION1 domain
% set aaa auth-provider active-directory-server sub1
domain subregion1.win.company.com authentication-prefix SUBREGION1| Element | Description |
|---|---|
| sub1 | Name of the Active Directory service |
| subregion1.win.company.com | Child domain of the REGION domain |
| SUBREGION1 | Authentication prefix that identifies the AD domain |
SUBREGION2 domain
% set aaa auth-provider active-directory-server sub2
domain subregion2.win.company.com authentication-prefix SUBREGION2| Element | Description |
|---|---|
| sub2 | Name of the Active Directory service |
| subregion2.win.company.com | Child domain of the REGION domain |
| SUBREGION2 | Authentication prefix that identifies the AD domain |
When you have completed the configuration of the authentication providers for the AD domains, use this CLI command template to show all the configured auth-providers:
> show config configuration context default aaa auth-provider
auth-provider {
local {
group admin {
administrator true;
jailbreak-permitted false;
}
user gateway_admin {
group admin;
password $6$BY0oSw7m$KHv2fmQHgn7OGyh5Vd.rw62.Jgx9Ho78FHyuOQJaviQLfAsY/LIe7SPYCgliweL7zYnoua1kXJGHn.DFdwOLM0;
}
}
active-directory-server sub2 {
domain-name subregion2.win.company.com;
authentication-prefix SUBREGION2;
}
active-directory-server sub1 {
domain-name subregion1.win.company.com;
authentication-prefix SUBREGION1;
}
active-directory-server region {
domain-name region.win.company.com;
authentication-prefix REGION;
}
active-directory-server servers {
domain-name servers.win.company.com;
}
}